Digital Twins Open Lecture 17 October 2025
Play Meets Policy - building secure simulations with privacy in mind
This course bridged game-engine prototyping and digital-twin telemetry with privacy-by-design. Students modeled data flows, implemented least-privilege auth, and practiced threat modeling (API risks, cheat/abuse vectors, logging/retention pitfalls).
Hands-on labs culminated in a playable or navigable scene wired to simulate sensor feeds, accompanied by a brief Security & Privacy Plan that documented controls, trade-offs, and monitoring measures.
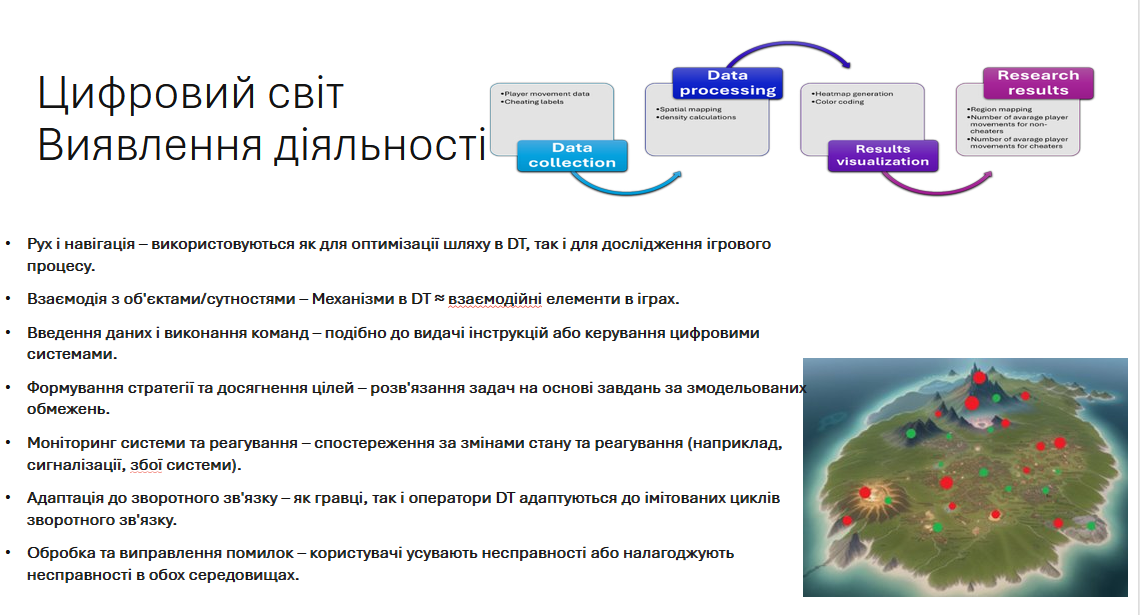
The Innovation Sprint - from risk discovery to mitigation delivery
A focused sprint adapted the Double Diamond approach to security work: Discover (asset & risk inventory), Define (priority threats), Develop (controls and tests), Deliver (demo and risk dashboard).
Teams presented before/after diagrams showing how IAM, configuration hardening, and log hygiene reduced the attack surface, without sacrificing learning value or usability.
Structured milestones, peer design critiques, and mentor clinics enhanced the maturity of student prototypes and institutional readiness for privacy-sensitive deployments.

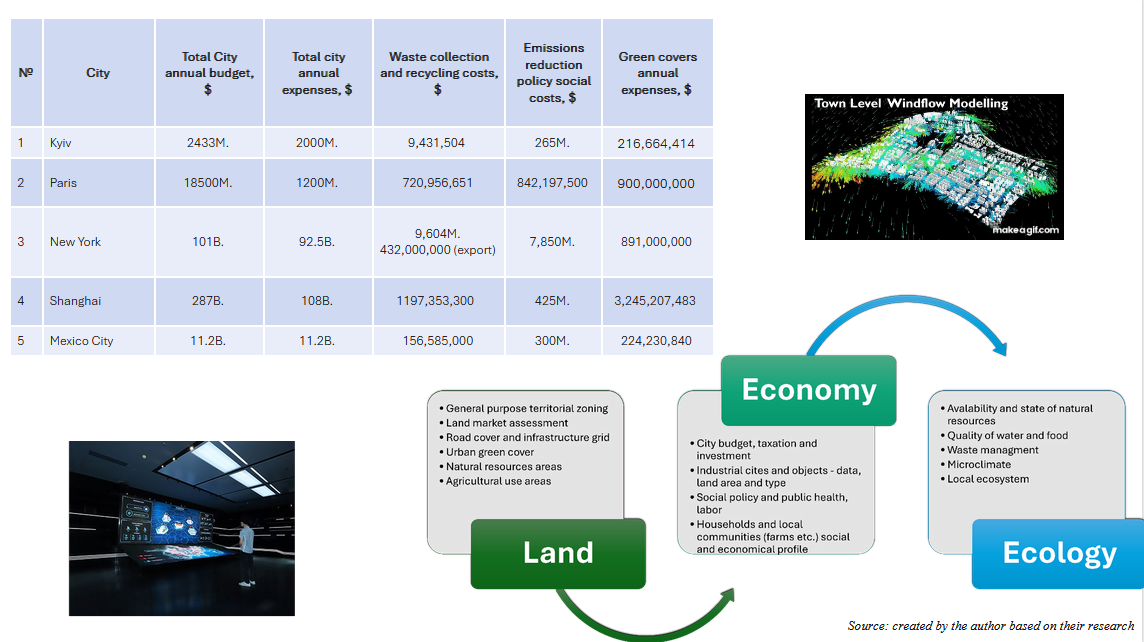
Lessons Learned - ethics, telemetry, and communicating risk
Students and faculty noted that clear rubrics for privacy and security, along with regular feedback loops, helped align technical ambition with ethical practice. Simple visualization of telemetry, alerts, access attempts, and retained data made risk visible and discussable for non-technical audiences.
Future iterations will deepen coverage of anonymization, introduce table-top incident drills, and expand guidance on consent & transparency in educational simulations.
Volodymyr NAZARENKO